SonarQube
Introduction
Since the management of projects, users and roles in SonarQube is supported. SonarQube is offered as an additional optional tool with full integration into DevOps-as-a-Service. The latest version of SonarQube s offered.
To use SonarQube to perform source code quality and security analyses controlled by Jenkins, two components are required:
- SonarQube server to perform analysis, evaluation, data storage, generate reports, define quality gates etc. To order it create a Service Request at the Servicedesk DevOps-as-a-Service. To activate SonarQube it's required to save every project in the DevOps portal first. After this step SonarQube can be added to individual users just by editing them.
- Sonar Scanner in Jenkins to perform the actual scanning of source code. The scanner transfers the intermediate results to the SonarQube server for analysis and evaluation. Since v2.6 the Jenkins Shared Library offers the automated creation of new projects on SonarQube, running the analysis on Jenkins and uploading the intermediate result for further processing to the SonarQube server.
Integration into Delivery Pipelines
Using Jenkins Shared Library
Since v3.0.0 of the Jenkins Shared Library, not only scanning maven projects, but also scanning all other types of projects is supported. Just use a Jenkinsfile as usual like e.g.:
sdcPipeline()
The library will automatically detect if SonarQube was configured on the Jenkins controller or not. If SonarQube is available and the branch you are building is the default branch (usually master) the first analysis stage will be Sonar Scan. Additionally, at the end, the pipeline will wait for Sonar Results. If the build does not pass the Quality Gate, the build will be marked as unstable.

It's possible to explicitly disable SonarQube for all branches by using a Jenkinsfile like:
sdcPipeline(sonarQube: false)
If this is the case, Sonar Scan is skipped and Sonar Results not called at all. The same happens if no SonarQube was configured in the Jenkins controller.

The sonarQube switch of sdcPipeline is true by default for the default branch. If you want to scan another branch, e.g. 'main' then a Jenkinsfile like the following one will do the job.
sdcPipeline(defaultBranch: 'main')
Please note that SonarQube in the Community Edition supports only one branch per project. And this branch will always be called 'master' in the SonarQube UI even if the real name is a different one.
![]()
If you have the SonarQube Developer or Enterprise Edition, you can enable scanning all branches like this:
sdcPipeline(sonarQube: true)
Jenkins Plugin
DevOps-as-a-Service includes the SonarQube plugin https://plugins.jenkins.io/sonar/ in its Jenkins controller. Documentation is available at https://docs.sonarqube.org/latest/analysis/scan/sonarscanner-for-jenkins/
The SonarQube plugin provides these added values:
- Injection of globally defined parameters (URL, project name, token, options...) into the build. This is used and handled by the Jenkins Shared Library.
- Furthermore, decorations for the build, as shown below in the table.
Screenshot from Jenkins | Description |
|---|---|
Integration of a SonarQube link at the repo/branch Jenkins page | |
Integration of a SonarQube link next to the build in the build list. The link forwards to the corresponding project/event in SonarQube server. | |
Jenkins can wait for analysis at SonarQube server and display the result of a quality gate in the pipeline view. The sonar result will be added to the repo/branch page below the Stage View. No further results or details will be available in the Jenkins UI. The SonarQube UI must be used to check results and define the quality gates. |
Using SonarQube
Browsing Projects
The portal offers a link to SonarQube for each project on the Homepage in the Source Code Quality tile
and on the Projects page in the Tools column
Click on SonarQube. If you have no existing session on your SonarQube instance, you will see the login page. Click the "Log in with keycloak" button to use the single-sign-on provided by the DevOps portal. That means if you're currently logged in to the portal, you will not need to specify your credentials again.

Now you are logged in to SonarQube. The search box was prefilled with the project name prefix. In the example it's DEVOPSAAS/. Therefore, you will see all SonarQube projects with results that originate from scans of git repositories.
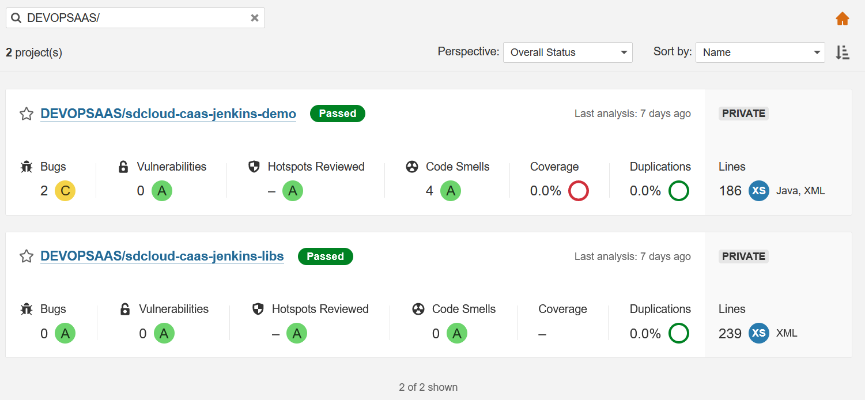
Instead of using the SonarQube links in the DevOps Portal you can also clear the search box and see all SonarQube projects in which you have at least a VIEWER role.
Project Roles
When a project is opened, different pages are available to work with it.

It depends on you role in the project which permissions you have.
Project Role | Browse | See Source Code | Administer Issues | Administer Security Hotspots | Administer | Execute Analysis |
|---|---|---|---|---|---|---|
| Admin | ||||||
| Master | ||||||
| Developer | ||||||
| Viewer |
Please note that "Execute Analysis" is usually performed in Jenkins. For more information, see above.
Due to security considerations, no user is allowed to directly administer a project in SonarQube. For more information, see below.
Managing Quality Profiles and Gates
There are two sections in SonarQube which are accessibly read-only for all logged-in users:
- Quality Profiles for each programming language.

- Quality gates, which decide if a build is ok or failed.

If the default settings do not fit for your instance, you can edit users in the DevOps Portal and add them to the sonar-quality-admins group by checking "Administer Quality Gates and Quality Profiles" in the SonarQube fieldset. Press Save when done.
The members of this group have read-write access to Quality Profiles and Quality Gates. It should be clear that you will need an internal governance so that sonar-quality-admins coordinate their work and communicate with the project admins.
To find out which Quality Profiles and Gate are used by a project, open the project and click on Project Information on the right-hand side.

Members of sonar-quality-admins can associate projects with other alternative quality gates that they have created themselves. The screenshot shows an alternative non-default quality gate. As you can see, the search box at the bottom can be used to find specific projects. Then simply use the checkmark to associate the project with the quality gate.

Plugins
By default, your SonarQube instance will have these plugins installed:
- Checkstyle
- Dependency-Check
- Findbugs (in fact, it's for SpotBugs)
- Groovy
- PMD
- SoftVis3D Sonar plugin
Commercial llicenses
To scan more than one branch per project and to get scan results shown in Pull-Requests in Bitbucket, the Developer Edition of SonarQube is required. The Enterprise Edition offers even more features, like e.g. additional programming languages or parallel processing of analysis reports. For more details, see https://www.sonarsource.com/plans-and-pricing/
Customers inside Deutsche Telekom can order commercial licenses at the Servicedesk DevOps-as-a-Service. External customers can bring their own self-managed SonarQube license.



